Overview¶
The goals of the authorization system are to:
Make Pulp safe as a multi-user system
Rely on User and Group definitions in the Django database, but allow them to come from anywhere
Enforce permission checks at each viewset using a policy based approach
Give users fine-grained control over each viewset’s policy
Architecture¶
Pulp’s authorization model has the following architecture:
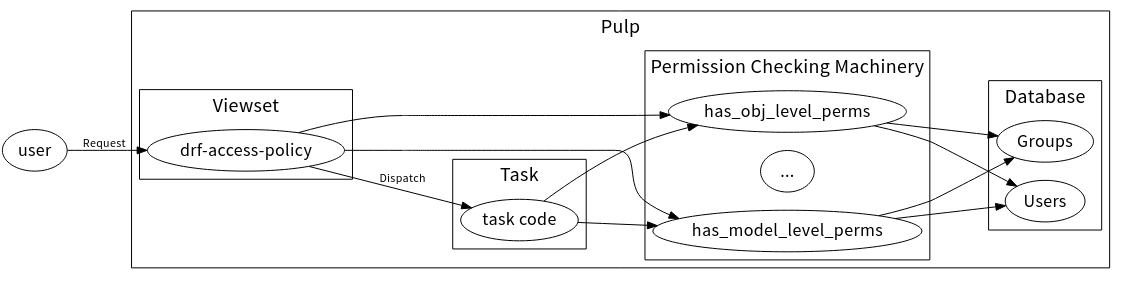
- Request Authorization:
Each request is authorized by a drf-access-policy based policy at the viewset-level. You can learn more about defining an access policy here.
- Task Permissions Check:
A permission check that occurs inside of Task code. This tends to use permission checking calls like has_perm or has_perms provided by Django.
- Permission Checking Machinery:
A set of methods which can check various conditions such as if a requesting user has a given permission, or is a member of a group that has a given permission, etc. See the Permission Checking Machinery section for the complete list of available methods.
- Users and Groups:
Users and Groups live in the Django database and are used by the Permission Checking Machinery. See the Users and Groups documentation for more information.
Getting Started¶
To add authorization for a given resource, e.g. FileRemote, you’ll need to:
Define the Policy:
Define the default
statementsof the new Access Policy for the resource. See the Defining an Access Policy documentation for more information on that.Define the
rolesas sets of permissions for that resource.Define the default role associations created for new objects using the
creation_hooksattribute of the new Access Policy for the resource. See the Adding Automatic Permissions for New Objects documentation for more information on that.Ship that Access Policy as the class attribute
DEFAULT_ACCESS_POLICYof aNamedModelViewSet. This will contain thestatementsandcreation_hooksattributes. Ship the roles as theLOCKED_ROLESattribute accordingly. See the Shipping a Default Access Policy documentation for more information on this.Add the
RolesMixinto the viewset and add statements for managing roles to the access policy. Usually this is accompanied by adding amanage_rolespermission on the model.
Enforce the Policy:
pulpcore.plugin.access_policy.AccessPolicyFromDBis configured as the default permission class, so by specifying aDEFAULT_ACCESS_POLICYit will automatically be enforced. See the Viewset Enforcement docs for more information on this.
Add QuerySet Scoping:
Define a
queryset_filtering_required_permissionattribute on your viewset that names the permissions users must have to view an object. This is possible if your viewset is a subclass of thepulpcore.plugin.models.NamedModelViewSet. See the Enabling QuerySet Scoping documentation for more information.